FortiSIEM Review: Unifying Security for Enhanced Threat Response
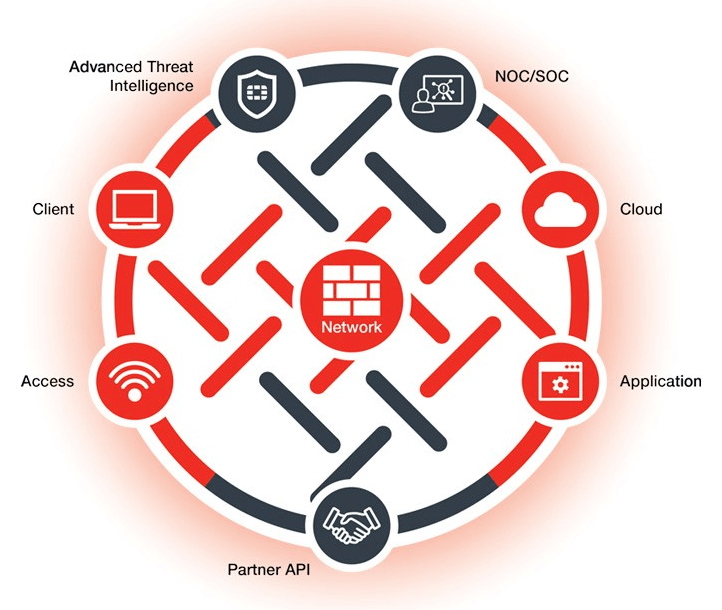
FortiSIEM Review: Unifying Security for Enhanced Threat Response Navigating today’s complex cybersecurity landscape demands more than just individual security tools. Organisations are overwhelmed by constant alerts, making it challenging to identify and respond to genuine threats. A robust SIEM solution is no longer optional but essential. This review explores how FortiSIEM addresses these challenges, offering […]
FortiSIEM Review: Unifying Security for Enhanced Threat Response Read More »