Top 3 Cyber Events That Matter in Australia – January 2026
Australia’s cyber threat environment continues to escalate faster than organisational preparedness. Despite years of warnings, recent data shows that many Australian organisations still struggle with basic cyber hygiene, timely patching, and governance of emerging technologies. Early 2026 has already delivered several incidents that expose these gaps, ranging from public sector breaches to actively exploited vulnerabilities and new regulatory guidance that many organisations are not yet equipped to follow.
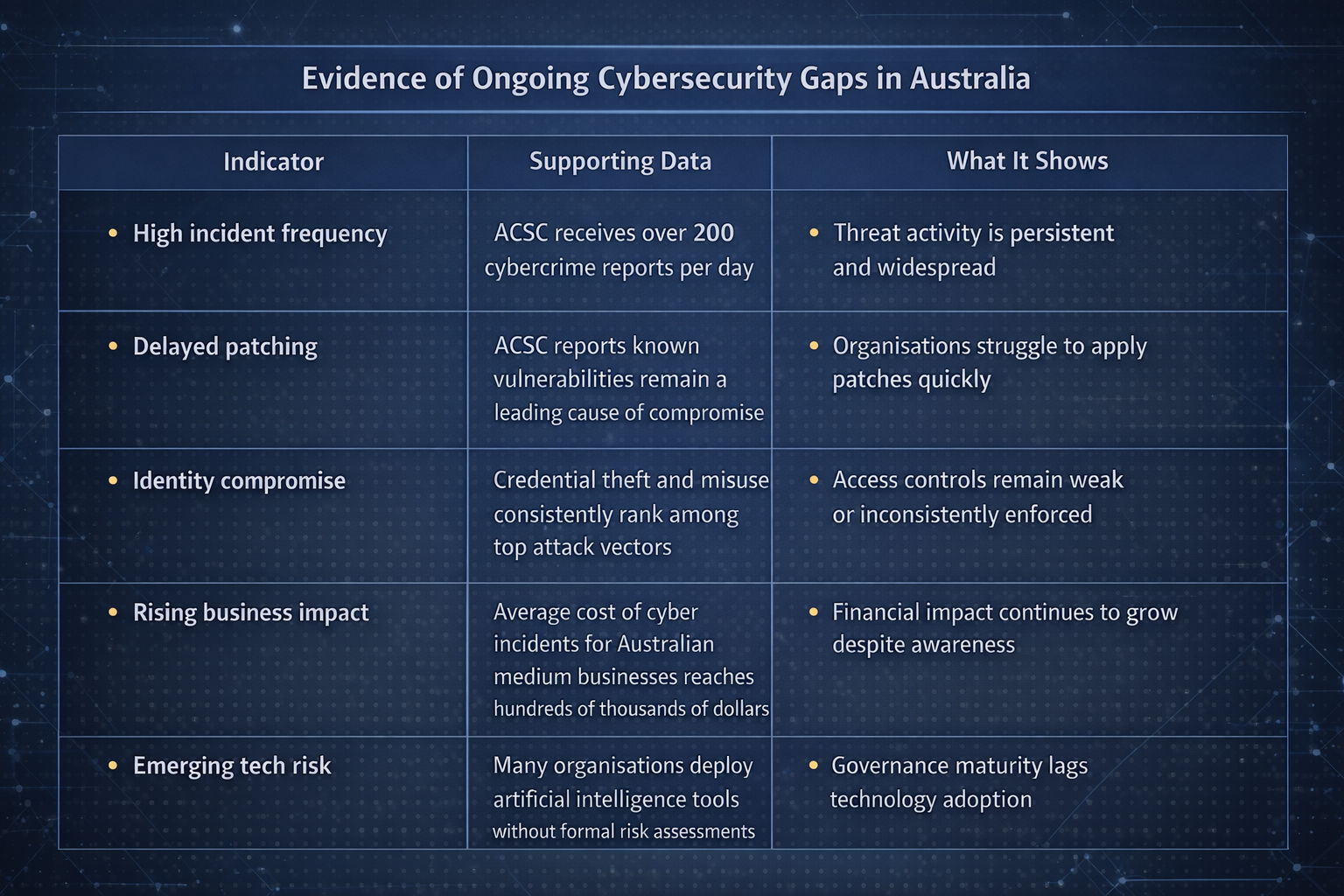
According to the Australian Cyber Security Centre (ACSC), it receives a cybercrime report approximately every seven minutes, and the average cost of a cyber incident to Australian businesses exceeds hundreds of thousands of dollars. Yet patching delays, weak identity controls, and poor visibility remain widespread across both public and private sectors.
The following three events highlight where Australian organisations are falling behind and why immediate action is required.
A DEEP DIVE INTO EACH EVENT

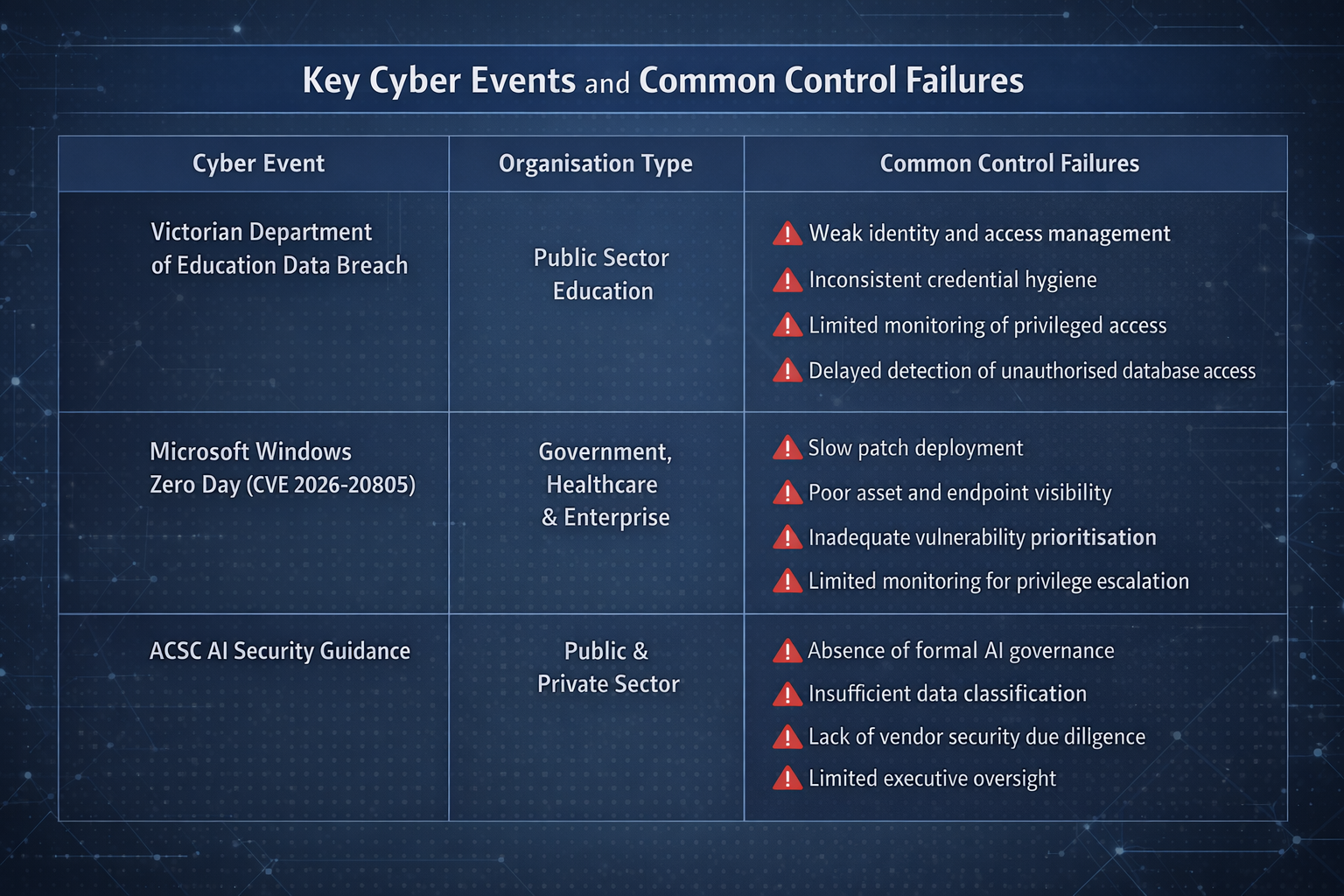
Victorian Department of Education Data Breach
Overview
In mid January 2026, the Victorian Department of Education disclosed a confirmed cyber breach affecting systems used by all 1,700 government schools across the state. Cyber actors accessed a database containing student names, email addresses, encrypted passwords, and year-level information for hundreds of thousands of students.
Source: insiconcyber.com
Why It Matters
Public sector systems continue to be a prime target for attackers due to their scale and often inconsistent security maturity. The ACSC has repeatedly reported that identity compromise and poor access control remain among the most common root causes of major government incidents.
Despite this, multi factor authentication and modern identity monitoring are still not consistently enforced across all government environments. The timing of this breach, just before the school year, further demonstrates how cyber incidents can quickly translate into operational disruption.
Impact on Australian Organisations
- Highlights ongoing weaknesses in identity and access management across large environments
- Demonstrates the cascading impact of centralised system failures
- Reinforces the need for proactive credential hygiene rather than reactive resets
Critical Microsoft Windows Zero-Day Vulnerability
Overview
In January 2026, a critical Microsoft Windows privilege escalation vulnerability was confirmed and actively exploited. The flaw, identified as CVE 2026 20805 under the Common Vulnerabilities and Exposures framework, affects the Desktop Window Manager and allows attackers to escalate access to SYSTEM level privileges after initial compromise.
Source: Lean Security
Why It Matters
The ACSC consistently reports that delayed patching is one of the most common contributors to successful cyber intrusions. In its most recent annual threat report, the ACSC noted that known vulnerabilities, often with available patches, continue to be exploited months or even years after disclosure.
The active exploitation of this vulnerability highlights that many organisations still lack effective patch governance, visibility of endpoint exposure, or the ability to deploy urgent fixes at scale.
Impact on Australian Organisations
- Exposes ongoing gaps in enterprise patch management processes
- Increases likelihood of lateral movement and domain wide compromise
- Demonstrates that basic controls remain a challenge even for critical systems

Regulatory Update: ACSC AI Security Guidance
Overview
In January 2026, the Australian Cyber Security Centre released new guidance on managing cybersecurity risks associated with artificial intelligence adoption. The guidance includes recommendations for internal AI usage policies, data anonymisation, and security assessments of AI vendors.
Source: digitalpolicyalert.org
Why It Matters
AI adoption across Australian organisations is accelerating faster than governance maturity. Industry surveys consistently show that many organisations deploy AI tools without formal risk assessments, security reviews, or executive oversight.
The ACSC has previously warned that emerging technologies are being adopted without the same controls applied to traditional systems, increasing the likelihood of data leakage, model abuse, and regulatory non-compliance.
Impact on Australian Organisations
- Reveals a governance gap between technology adoption and risk management
- Increases exposure to data privacy and intellectual property risks
- Signals rising expectations for board-level accountability over AI usage
KEY TAKEAWAYS FOR AUSTRALIAN ORGANISATIONS
- Cyber incidents continue to succeed due to preventable weaknesses such as poor identity controls and delayed patching
- Large-scale public sector breaches show that maturity gaps persist even in high-visibility environments
- Regulatory guidance is expanding into emerging technologies, but many organisations lack the structures to respond effectively
The pattern is clear. Threat capability is advancing faster than defensive maturity. Until Australian organisations close gaps in fundamentals such as access control, patching discipline, and governance, these types of incidents will continue to escalate in frequency and impact.
If you want, I can also provide a short executive summary with statistics only, or a board-focused risk narrative tied directly to governance obligations.
THE IMPACTS
More from this months newsletter >
Cyber News Wrap-Up January: Key Cyber Security Stories
CYBER NEWS WRAP-UP: JANUARY 2026 Welcome everyone to the first cyber recap of the year! […]
Security Platform Updates: SendSafely HALO and Agile Blue Enhancements
SOLUTION UPDATES & NEW FEATURES At CommuniCloud, we actively monitor updates across our security solutions […]
February 2026 Cyber Threats Australia: MITRE ATT&CK + Essential Eight
MITRE ATT&CK & ESSENTIAL EIGHT ALIGNMENT Aligning MITRE ATT&CK with the Essential Eight helps organisations […]
IRONSCALES Email Security: Adaptive AI, Human Intelligence, Real Defence
Spotlight Feature | Ironscales: Modern Email Security Built For How Attacks Actually Happen Email remains […]





